Single Sign-On: How to Master Microsoft 365 & New Policies!
Password Policies and Single Sign-On in Office 365 – Balancing Security and Usability
Managing account access and authentication is a critical concern for businesses. The implementation of password policies and Single Sign-On (SSO) systems, particularly in environments like Office 365, requires a careful balance between security and user convenience.
This article explores the benefits and challenges of enforcing password policies through Group Policy, as well as the advantages and potential drawbacks of using Single Sign-On for Microsoft Office 365 and office networks. It also touches on recent changes to security and the use of 2factor to supplement these modern methods.
Group Policy
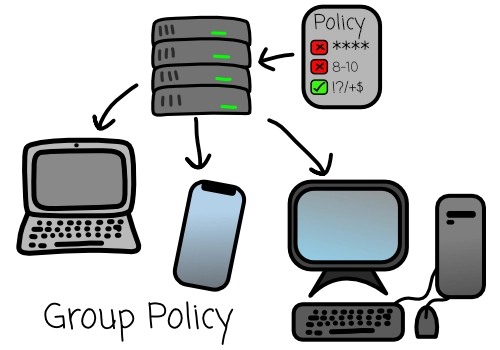
Group Policy is a vital server-based tool used for efficiently managing settings across a computer network within a domain (in simple terms it manages settings applied to users and groups of an organisation/business).
One of its key applications is in enforcing password policies for domain logons. Through Group Policy, administrators can set specific requirements for user passwords, such as minimum length, complexity requirements, and the frequency of password changes, relevant to the requirements of the company and their chosen security protocols.
This approach ensures a standardized level of security across all users within the domain. By enforcing changes at regular intervals, potentially compromised passwords are refreshed and taken out of the equation, thus reducing the window of opportunity for unauthorized access. Complexity requirements are primarily to prevent users from choosing easily guessable/crack able passwords, adding an additional layer of defence against common brute-force attacks which are becoming more and more prominent.
However, something that is important to consider is to balance this security with usability. Overly stringent policies can lead to user frustration and can in turn have negative effects, potentially leading to insecure practices like writing down passwords! A big no-no…
Recent security findings suggest there has been a significant shift towards longer phrases used for passwords rather than frequent password changes and the use of multi-factor authentication for enhanced security instead.
Here are some of the Benefits and Negatives of password policies via group policy.
Benefits:
- Enhanced Security: Strong password policies enforced through Group Policy help prevent unauthorized access by ensuring passwords are complex and changed regularly.
- Consistency Across the Network: Implementing policies through Group Policy ensures uniform security standards across all users and systems within the network. The changes are enforced to everyone and cannot be set / tampered with by the users.
- Automated Enforcement: Group Policy automates the enforcement of these policies, reducing the need for manual checks and increasing overall compliance.
Negatives:
- User Inconvenience: Frequent password changes and complex requirements can lead to user frustration and reduced productivity, as employees may struggle to remember their credentials.
- Increased Support Calls: Stringent password policies often lead to an increase in support requests due to forgotten passwords or account lockouts.
- Potential for Weaker Passwords: Ironically, frequent password changes can lead users to choose weaker, easier-to-remember passwords or use predictable patterns in their password creation, it is important to avoid pushing users down the route whereby they will generate simple passwords to help them remember them!
Single Sign-On (SSO)
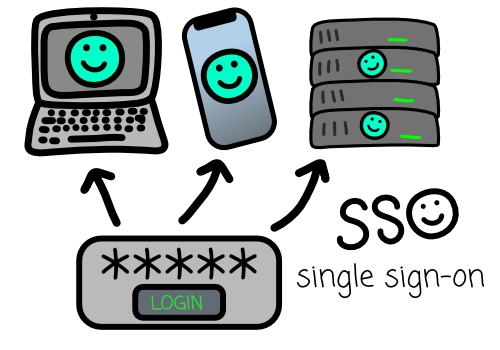
Single Sign-On (SSO) is a user authentication service that allows a user to use one set of login credentials (e.g., name and password) to access multiple applications. The main benefit of Single Sign-On (SSO) is its ability to simplify the management of numerous usernames and passwords, significantly enhancing user convenience and experience. When implemented, SSO provides a relatively seamless workflow for the user.
It works by authenticating the user for all the applications they have been granted access to and eliminating further authentication prompts when they switch applications during a particular session.
All in all, it sounds like a great solution for an end user, however there are some things to consider as if it is not setup and configured properly the end user could easily become a hacker’s dream, allowing access to multiple accounts after one single compromise!
Main benefits and Negatives of Single Sign-On for Office 365 and Office Networks
Benefits:
- Streamlined access: SSO allows users to access multiple applications, including Microsoft Office 365 and other network resources, with a single set of credentials.
- Improved user experience: Single Sign-On (SSO) simplifies the user experience, reducing password fatigue and the need to remember and manage multiple sets of credentials.
- Arguably provides enhanced security and compliance by reducing the number of passwords, SSO can decrease the chances of password-related breaches. Additionally, it provides better control over user access, aiding in compliance with various security standards.
Negatives:
- Single point of failure: With Single Sign-On, if the primary login credentials are compromised, it potentially gives attackers access to all linked applications and services.
- Complexity in implementation and management: Setting up SSO can be complex, requiring integration across various systems. It also demands ongoing management to ensure seamless and secure operation.
- Dependency on network connectivity: SSO systems often rely on continuous network connectivity. Any network issues can therefore hinder access to all connected services.
Recommended practices.
Traditional approaches like frequent password changes are being reevaluated. Microsoft 365, a leader in cloud-based productivity, recommends a more modern approach, focusing on Two-Factor Authentication (2FA) rather than enforcing regular password changes.
Microsoft 365’s Security Recommendations
Moving Away from Frequent Password Changes:
As we just mentioned, historically, regular password changes have been a staple in security policies. However, this practice often leads to weaker passwords as users tend to choose simpler, easily remembered (and thus easily guessed) passwords, or make minor modifications to existing ones. Microsoft 365’s stance reflects a growing consensus in the cybersecurity community that frequent password changes do not necessarily enhance security as much as traditionally thought.
Emphasis on implementation of Two-Factor Authentication:
2FA adds a significant layer of security, requiring the end user to provide a code or authentication using something they have in their possession (like a smartphone app or security token). This approach is much more effective in preventing unauthorized access because even if a password is compromised, an attacker still needs the second factor to gain access.
The Advantages of Implementing 2FA in Microsoft 365
Enhanced Security Against Breaches:
- With 2FA, the chances of unauthorized access are drastically reduced. Even if a password is stolen or phished, without the second factor, it’s rendered completely useless to attackers.
Streamlined User Experience:
- Users no longer need to remember and regularly change complex passwords, which can be a source of frustration and reduced productivity.
Better Compliance with Security Standards:
- Many regulatory bodies now recognize 2FA as a critical security measure, and its implementation can help organizations comply with various data protection laws and standards. It helps with obtaining insurance at better rates and may even secure your company deals with other clients as you show your buisness to be more professional and serious about security.
Integrating 2FA in Microsoft 365: Steps for Businesses
Implementation
Educate Employees: Start with training sessions to educate employees about the importance of 2FA and how it will impact their daily workflow.
Choose the Right 2FA Method: Microsoft 365 supports various 2FA methods, such as phone calls, text messages, or authenticator apps. Choose the one that best suits your organization’s needs. There is a lot to consider in terms of how tight security needs to be for your company, and whether this tight security will impact usability and productivity.
Regularly Review and Update Security Protocols: Stay informed about new security threats and update your 2FA methods accordingly.
Challenges and Considerations
Dependency on Secondary Devices:
- 2FA requires users to have access to their secondary device or method (like a phone or security token), which could be a challenge if the device is lost or inaccessible (they forgot it at home or so on).
Potential for User Resistance:
- Some users might resist the change, especially if they are not tech-savvy or are accustomed to the simplicity of just a password. They may also object to having it installed on their personal phones! In the case of this it is possible to setup sip trunks and lines to link to business phones already on site (FBS can certainly help with this requirement!)
Microsoft 365’s recommendation to prioritize 2FA over traditional password change policies really highlights a big shift in cybersecurity methods and strategy. This approach aligns with the modern understanding that robust security must be both user-friendly but also strong and difficult to exploit.
At FBS, we are dedicated to helping businesses navigate this transition, ensuring they can leverage Microsoft 365’s capabilities securely and efficiently, whether or not they decide to use single sign on for their business going forward! Make sure to get in touch if this article has left you with any questions or concerns.
Don’t forget to follow us on LinkedIn, and YouTube, for updates! Or click here to return to the Blog Page.
